Long-time NR reader and contributor Horshack found a major vulnerability in Nikon’s C2PA feature on the Z6 III camera (released a week ago). Here is his report:
Update:
I’ve found a way to circumvent the C2PA protections on the Z6 III using the camera’s multiple exposure feature.
For those unfamiliar, this feature lets you take multiple exposures and have the camera blend them together into a single out-of-camera jpg file, using one of several blending modes “Add”, “Average”, “Lighten”, or “Darken”.
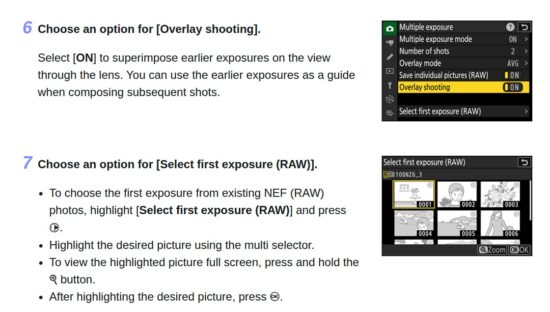
The feature has an overlay option that lets you specify the first exposure to blend, using an existing raw file on the media card. Here is the description of this option from the Z6 III manual:
Normally you’d select an image taken with the same camera as your overlay but the feature will let you select any valid Z6 III raw image that’s on the media card, including those taken with another body.
If you pick a raw from a non-C2PA enabled Z6 III as your overlay image and then use that raw with the multiple-exposure overlay feature on a C2PA-enabled Z6 III, the resulting jpg produced by the multiple exposure feature will have the C2PA credentials of an image the camera didn’t take.
What’s worse, if instead of taking the photo with the non-C2PA enabled camera you instead generated the image with AI and stored it in bayered form over an existing valid Z6 III raw you can have the C2PA-enabled camera sign AI photos, completely circumventing the C2PA protections in Nikon’s implementation.
Here are the steps for a proof of concept I’ve done demonstrating the vulnerability:
- I have two Z6 III’s – Body A is the non-C2PA “imposter”, Body B is C2PA-enabled
- I generated a graphic in Photoshop that reads “Hacked by Horshack”. I took a photo of that graphic using the imposter body. But keep in mind we could’ve also generated this NEF by programmatic means without any camera and stuffed the generated image data it into a valid NEF – I just haven’t written that software to do it.
- I moved the media card from the imposter body into the C2PA-enabled body
- On the C2PA-enabled body I enabled the Multiple exposure feature, set the “Number of shots” to 2, “Overlay Shooting” to ON, “Overlay Mode” set to Light, and “Select first exposure (RAW)” to the imposter NEF on the media card
- I then shot a blackframe with the C2PA-enabled body, ie an image with the lens cap on.
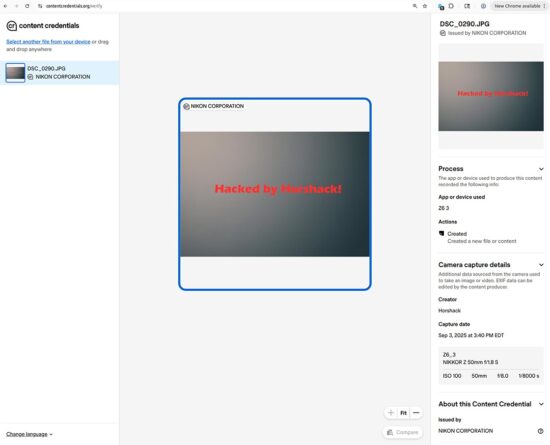
Here is the resulting jpg the C2PA-enabled body produced, which is identical to the imposter image from the non-C2PA enabled body since it combined the imposter NEF with an empty blackframe on the C2PA-enabled body:

And here is the C2PA verify report for that out-of-camera jpg, from the CAI’s online verify tool:
This demonstrates the dangers of “soft targets” in a C2PA-enabled system. Obviously I haven’t compromised the underlying C2PA cryptographic mechanism itself but instead found a way to circumvent it entirely by using an existing camera feature that hasn’t been hardened against soft attacks like this.