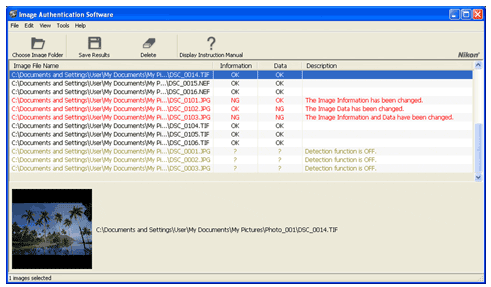
ElcomSoft was able to crack Nikon’s Image Authentication System (priced @ $489). They were able to extract the original image signing key and use it in several forged photographs that successfully pass Nikon Image Authentication Software validation:
“Nikon’s implementation of image authentication has a major design weakness. ElcomSoft researchers discovered a flaw in the way the secure image signing key is being handled in camera. The vulnerability allowed the researchers to actually extract the original signing key from a Nikon camera. This, in turn, made it possible to produce manipulated images with a fully valid authentication signature. By using the signing key, ElcomSoft has prepared a set of hoax images that successfully pass validation with Nikon Image Authentication Software.”
All Nikon DSLR models that support Image Authentication are affected, including Nikon D3X, D3, D700, D300S, D300, D2Xs, D2X, D2Hs and D200. ElcomSoft provided several examples of manipulated images that would be authenticated as original:
Via Net-security